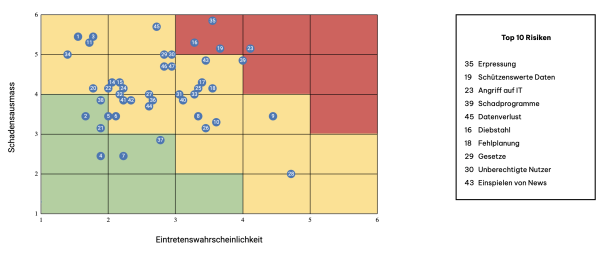
Apps with love has been ISO/IEC 27001:2022 certified since December 2023. This strengthens our safety and quality standards. It is our third ISO certification in addition to ISO 9001 for our quality management system and ISO 14001 for our environmental management system.
A certification such as ISO 27001 primarily says something about how, or to what extent, a company deals with aspects of information security. A certification in itself only provides very limited security: the key question is how processes, guidelines and best practices are actually implemented on a daily basis. An ISO certificate is therefore primarily an indicator that we as a company are addressing information security issues. Of course, we have done this before, but the certification forces us to scrutinize all relevant aspects systematically and in a process-oriented manner. This blog post describes what these aspects are, how the certification process works and what we have learnt in the process.